#Introduction to hyper-v on windows 10
Explore tagged Tumblr posts
Text
Role of social media in the Fashion Industry
Acknowledgment
It is always a pleasure to thank all who have been a part of my capstone project journey. This project was a part of my specialization course which gave me a wonderful opportunity to interact with the people of the fashion industry and other experts.
Firstly, I would like to express my gratitude to my parents who always encouraged me to take risks in life and are the pillars of my strength. Without their encouragement I may not have been able to complete this project.
Secondly, I would like to convey my deepest thanks to Bennett University and my mentor Prof. Sumita Vaid Dixit for providing invaluable guidance, suggestions throughout the project, and by helping me in putting this project together.
Thirdly, a big thank you to fashion experts Mr.Rahul Toppo from Chennai, Ms. Kriti Chawla fashion stylist from Popexo, NIFT graduate Prof Pratik Kumar Singh, Prof. Neelam and Kashish from Ranchi who is an aspiring fashion designer. Their opinions and insights helped me get a better perspective of the fashion industry.
In the end, I would like to thank all those who I have not been able to name in the acknowledgement but they have played an important role in my project. Personally, the opportunity to write this capstone project is a big milestone in my career development. I hope I'm able to get another opportunity to interact with all of you again.
Sincerely,
Rishika Singh
LA17MC061
Introduction
India's fashion industry is currently estimated at $70 billion, of which up to $9 billion is already digitally influenced, as in, shoppers are searching, browsing, and buying stuff online. Globally, and in India, fashion is the third most-followed topic among Instagram users after (movies and music).
Kashish from Ranchi who is aspiring in Fashion designing has said that being in the fashion industry and neglecting social media can be a great loss for anyone's career. "Social media plays a very important role, helps in learning the new trends, and motivates us to create good content, " she said.
Over the past few years, social media and digital media have drastically changed how people consume the content or any sort of news, especially in the fashion industry. Both fashion blogs and social media have recently made an elitist industry more available and relatable to regular customers. Social media has created an open channel of communication between organizations and citizens. Nowadays, content is expended online and individuals are not only reading content, but they are giving their inputs through comments and social media. Numerous sorts of fashion blogs overseen by regular people are giving customers an interior look into what utilized to be an elite, fashion-experts-only industry.
Rahul Toppo, a fashion designer from Chennai said, “Social media platforms play an important role in fashion today, we can showcase our collection, content, designs and we can connect and reach to many people”. Some of the young designers like Amit Aggarwal, Dhruv Kapoor, and many more are tapping on social media mainly active on Instagram.
CHAPTER 1
Why are the fashion designers tapping in the world of social media?
In 2012, Facebook spent $1 billion to acquire what was then just a photo-sharing app. Over the years, however, Instagram has not only added a slew of features that attracts more users but also become a marketing and selling platform for business.
Everyone has been obsessing over the old designers like Manish Malhotra, Sanjay Garg, Rohit Bal, and Sabya Sacchi for forever now. Even though they’re evergreen designers in India who all the people in the country wish to wear and admire. The designs and work of these legendaries have always inspired others to work more and more and know the audience wants. The Indian customers are now becoming modernized and more open to the labels from such upcoming Indian fashion designers.
Preeti Verma, founder of an Indie label Runaway Bicycle, managed to go courtesy Instagram. Verna says keeping her Instagram buzzy and updated is more work than managing the website of fashion.“We put a great deal of thinking into our Instagram feed. We have a writer and an art director who manage the quality of content. We shoot our products specifically for the app. We push out one post every day, and it certainly is a more live medium to maintain, unlike our website,” she said.
Pratik Kumar, a professor of Fashion Designing has stated, “I’m in this fashion industry for around 10 years now and can say that in the early time, designers lacked the internet, the age of information technology but now everything is digitized and even the industry is turning into robotics.”
Manish Malhotra talks of fashion in the age of Instagram, “Brand experience today is just a click away. Digital media has revolutionized a hyper form of window shopping. Earlier, the only people privy to what I was showcasing were those who attended the show or came across it in the newspapers the next day. Today, everyone has a front-row seat to my shows via Instagram, Facebook, Twitter, and Livestream.”
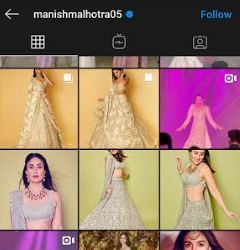
Caption: The instagram account of Manish Malhotra (Source: Instagram)
What advantages do Social media have?
Fashion brands on social media, it is a modern platform for interaction between brand and customer. Before the arrival of the internet, all the programs for launching any design or any clothes or any brands were done through glossy magazines, TV, etc. And social media is ruling many facets of businesses and their impact on their lives is enormous.
It gives low to zero overhead cost
There’ll be no need for expensive expenditures any more in the digital area. Creating and implementing top social media campaigns and strategies are free and cost-effective. Signing up and making a profile on popular social media platforms such as Facebook, Instagram, Pinterest, etc is completely free.
It increases customer engagement and loyalty
People spend a lot of time on social media, it's not a tough task to attract new consumers through social media. Social media allows us to interact with recent customers and old customers, but what keeps them loyal? It is the content that the user posts on their social media platforms.
It reinforces brand awareness and credibility
Social media is the best platform to showcase the fashion studio and it acts as the best medium for brand recognition. Enhance the brand’s awareness and increase the following in all social networks such as Facebook, Instagram, LinkedIn, Twitter, and Pinterest by presenting all the designer collections.
Social networks impact buying decisions
The vast majority of the individuals look for designing trends and latest fashions and are aware of them through social networks only. It acts as a word of mouth so any matter can spread in no time. The business pages' preferences, shares, remarks, and so forth will impact and be an immense effect on the clients' buying choices.
Demographic targeting
Millennia is the targeted customer for the fashion industry and social media could be a customized stage where fashion retailers can target the audience demographics wise such as sex, age, area, hashtags, etc. Other than, it is exceptionally simple to track client behavior patterns online.
It is an effective marketing tool
Whether anyone wants to get high traffic, brand loyalty; provide better customer service; increase sales volume, social media acts as a marketing tool for the fashion and apparel industry.
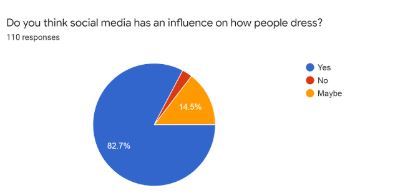
In the survey of 110 consumers, 82.7% agree that social media is the biggest medium from which they get influenced.
Kashish from Ranchi who is aspiring in Fashion designing stated, “I have just started my journey and Instagram is really helpful because it helps me in reaching more and more people and I can create a good gallery by posting pictures and videos. I am also learning from other designers as well as knowing the latest trends.”
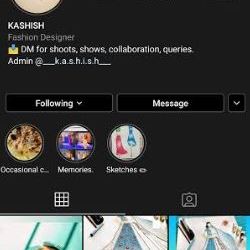
Caption: Kashish trying to engage with the audience by posting her designs on Instagram (source: Instagram)
The best media to target people for promoting various designs and labels on this Pratik Kumar has mentioned, “We can use any media whether its Instagram, Facebook, Pinterest or twitter but it all depends on the targeted consumers. For example, if we target the age group of 15-25 then they’ll be mostly on Instagram but if we target the age group of 35- 50 they’ll be mostly on Facebook. So the use of media depends on the targeted consumer. ”
Neelam Patel from Ghaziabad who is a client in fashion designing and also a professor. She says, “I won’t prefer to promote as I am not a designer but being a client I would prefer Pinterest as they cater a large segment under one roof. I don’t have to like and follow the pages for what I want but by just one keyword I will type and find lots of options related.”
https://www.youtube.com/watch?v=wDNaZgCYzkM&feature=youtu.be
Caption: Kriti Chawla currently working in Popexo as Fashion stylist has expressed her views on the importance of social media in Fashion industry.
Social media has transformed the shopping process. From research to brand interaction to promoting the designs to actual purchasing processes, the entire situation has seen significant changes.
CHAPTER 2
The Impact of fashion industry on people and on market
Success story of Kresha Bajaj Zaverias a famous fashion designer
Kresha Bajaj Zaveri, an Indian Fashion designer was born in Mumbai, India on March 7, 1988. Kresha has studied fashion from London College of Fashion, Parsons New York, Parsons Paris, FIDM Los Angeles, and now try to bring all that knowledge to the streets of India. Fashion designer, influencer, and hairess whose clothing line Koesch and Haute taste have won her commercial success and a huge following on social media. She has over 168,000 followers on Instagram, and her stories on Instagram and her posts encouraged and gathered the attention of fashion publications like Elle Magazine. Her designs have been showcased in the Lakme Fashion Week 2014.
Koesch originally started as a website in 2013 and specializes in bespoke western and bridal women wear. She’s famous for what is called her “LOVE STORY LEHENGAS” where they map out the couple’s journey on the garment bringing alive their love story.

Caption: Kresha Bajaj Zaveri (source: Instagram)
In her blog, Kresha has shared her experience with social media for her career and she thinks that luxury and social don’t go hand in hand. “Social media platforms, and in my case Instagram specifically, being an extremely visual platform is the perfect tool to create an online presence for Krésha Bajaj, the brand”, says Kresha. Kresha believes to post the original content, ensuring that it is attractive enough for people to gush over it.
On social media, the feel, the look, the textures of the fabric will be missing. Not only on social media but no online shopping websites or apps can give that feel or the emotion of the fabric or the material of the cloth which is given in the stores or the showroom of these clothes. As Kresha’s store is only in Mumbai and she says, “it is important for us to help an online viewer feel that they are in actual space while browsing through our online posts.”
Kresha wants her consumer to believe in their imaginary world of dresses of their choices and on this she said, “For us, we want to use Instagram as a look book of a wonderland that people enter through their phone, but feel the need to come to explore in person. ”
Only posting good content, and promoting designs are not enough. According to Kresha, to gain more and more consumers and their attention the important thing is to engage with the audience, answering their questions and giving them as much information as necessary. Having a beautiful page is irrelevant if it doesn’t garner the right kind of attention and encourages conversation.
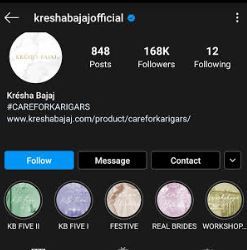
Caption: Kresha Bajaj promoting her brand by posting her designs and modals on social media (source: Instagram)
Marketing of fashion in the market in this decade
In this modern era of cut-throat competition, it is important to take care of every aspect related to marketing in the fashion world. The word media indicates the meaning of the main source of communication, these can be in the form of writing, images, visuals with narrations, or clips. Now, talking about the media there are many mediums from which the message of the designer or any influencer can be sent to their consumers and can attract more and more audiences.
Mediums like radio, television, newspaper, banners, billboards, websites, magazines, social media, or fashion show events like these. In this passage of time fashion has made its place in the culture, slowly and steadily people are accepting and following the latest trends and want to know the updates and latest upcoming fashion which is mostly provided by various mediums.
Television has a wide influence on its viewers.it affects not only, the knowledge of the audience but also the attitude towards many things. For example, the desire for the products and their brand preferences have been changed. In general, TV has higher credibility than newspapers, People are most likely to believe in what they see, not what they read. TV as a medium influences the dressing of youths. Audience members tended to make changes in their appearances, value, attitudes, and other characteristics to become more like the admired celebrities.
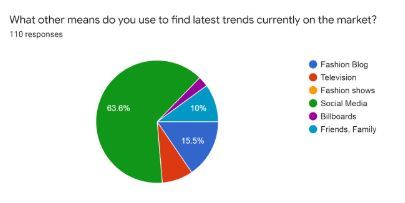
This data suggests, most of the consumers find their latest trends of fashion which is going on the market from social media then comes to fashion blogs and friends' families and then goes on.
In magazines, more than any other medium, advertisements and editorial content flows together to create an experience.
Magazines, being the media that attracts the most specialized audience can have a powerful impact on its niche audiences. Vogue, Lucky, W and many more are the most readable fashion magazines. Women are the most targeted for this medium of fashion. For women especially, reading magazines is related to the internalization of societal ideals and self-objectification.

Caption: Priyanka Chopra being featured for the cover page of Vogue India Magazine (Source: Pinterest)
In the Fashion show, in the first era of the fashion industry, designers had to show their new designs to the client through sketches. At that time, fashion designers used fashion dolls which are also known as dummy; this was the only medium to illustrate the new upcoming designs. In the second era of the fashion industry, the fashion dolls or the dummies were replaced by the living mannequin and then the models gave an entry in the fashion industry.

Captions: Soha Ali Khan walking gracefully on the rampwalk (source: pinterest)
Celebrity has backed the fashion industry
Taking cues from international celebrities, Indian film actors and cricketers are increasingly launching their own clothing and accessories brands to cash in on a category that industry executives and analytics believe has remained untapped so far in the country. Social media like Snapchat, Instagram, Facebook, Twitter and more all the inextricable parts of being famous in today’s world.
In the survey of 110 consumers, 85.5% believed that the consumers are influenced by their favorite celebrity. In this survey, most of the consumers were attracted towards lead actors like Shahid Kapoor, Hritik Roshan, Sonam Kapoor, Alia Bhatt and many more.
Chapter 3
Future of the fashion industry
The year ahead is likely to be challenging. Winds of change are sweeping the fashion industry, and many markets are set to see slower growth and declines in consumer confidence. Indian consumers and their apparel preferences are gradually changing, which in turn is altering the shape and size of the apparel business.
Indian customers and their apparel choices are gradually changing, which in turn is altering the shape and size of the apparel business. The changing demographics and psychographic profile of he Indian customers is today, supported by the apparel market which is moving away from tailor-made clothes to ready-made clothing. In India, people are shifting from rural to urban areas in search of jobs and some to find better education at a continually increasing rate. By 2025, the middle class consumers which will form 48.5 percent of the total targetable consumer base will contribute about 55-60 percent share of the apparel market size.
The increasing access to digital devices and internet is enabling the masses to have online shopping experience irrespective of whether they are living in urban or rural areas. The market growth and continuous shift towards brands will support new ventures, given the strength of the product and a clear growth strategy based on real consumer insights.
How do the fashion industry is coping with COVID-19 pandemic?
Several apparel makers and fast-moving consumer goods companies had stepped up to produce medical-grade masks as philanthropic acts when Covid-19 struck but now it is apparent that the pandemic is set to alter lifestyles at least some time to come.
“Masks are expected to become a habit over the next few months. We are also working on neem and tulsi treated fabrics for Peter England for a greater degree of wellness,” said Vishak Kumar, CEO of Madura Fashion & Lifestyle. The covid-19 pandemic has created a crisis across all the business barring those of essential commodities. India’s largest fashion body, theFashion Design Council of India (FDCI) cancelled its bi-annual ready to wear fashion week in early March 2020.
Shopaholics, on their part, are keeping their shopping carts ready for delivery once the lockdown for Covid-19 gets over.
Delhi-based fashion designer Manish Tripathi designs khadi face masks to fight with this covid-19 pandemic.“I am preparing these masks for the people who can’t afford to buy masks. Then I will try selling them online and whatever amount is collected will be contributed to the PM-CARES Fund to fight the coronavirus,” he said. In his social media (twitter) account he promoted his idea and social work.

Caption: Manish Tripathi contributing in this covid-19 pandemic (source: Twitter)
“Make your social media more creative. This is the perfect opportunity to redesign your Instagram or declutter your desktop. Tidy up your photo gallery and, most importantly, unburden your Whatsapp media”, says Fashion designer Abhishek Dutta.
Popular fashion designer Manish Malhotra is known to share his eccentric work across social media platforms and this time he used his social media account to engage his fan following by showing them a throwback of one of the famous fashion shows. In this amid Covid-19 lockdown, the ace fashion designer has shared an unseen picture from his early days in the industry which has taken social media by storm.
In Instagram, he posted a throwback picture of back in the days when he was a model. He also dropped the sweetest picture featuring Aishwarya Rai Bachchan in the fashion show and is setting friendship goals.

Caption: Manish Malhotra with Aishwarya Rai Bachchan in the fashion show #throwback (Source: Instagram)
Since India went into lockdown on 24 March, it seems more and more of the people are turning to social media to consume news and communicate with their friends or to see what is trending whether it is fashion or any other source of entertainment.The first week of the lockdown saw citizens spend more than four hours a day on social media — an 87 percent increase compared to the previous week, as per a poll conducted by Hammerkopf Consumer Survey.he poll conducted on 28 March with 1,300 respondents in New Delhi, Mumbai, Bengaluru and Chennai found that 75 percent of people spent more time on Facebook, WhatsApp and Twitter compared to the previous week, largely to consume news and remain in touch, and that social media usage jumped from 150 minutes per day prior to the lockdown to 280 minutes a day during that first week.
“As everyone knows due to COVID -19 most of the businesses are in the worst situation. The fashion industry is one of those. Stores are closed and all agreements are stopped”, says Rahul Toppo a fashion designer. He also stated, “It will take time to recover But there is a good advantage for social media as due to lockdown everyone is spending more time in social media like Instagram, Facebook & YouTube, many brand and designer are connected to their followers they are using this time to promote their present & previous work, as we are also connected to our followers showing illustration, design process all behind the scenes and promoting previous work”.
Conclusion of the project
The world is becoming digital and with the advent of information technology, the ways of communication and work have been revolutionized completely. over the last decade, social media has become an effective marketing tool, it has not only created a new dimension of marketing but also provided many opportunities to the marketers to create brand awareness among consumers.
Social media is a compilation of online platforms and communication channels that are used to share information, profiles, promotion of any sort of event or designs, or any exhibition.
The fashion industry will get great help through social media to reach a height and can attract more and more consumers.
Bibliography
This project has been written with the help of multiple articles that have been proven as a credible source. And with the help of survey of 110 consumers which was conducted by the writer.
Chapter 1
Livemint
https://www.livemint.com/Industry/jtjpWRTMUqKRvtT72sX1PJ/Digital-footprint-in-Indias-fashion-market-more-than-double.html
Economic Times
https://economictimes.indiatimes.com/tech/software/how-instagram-is-driving-fashion-business/articleshow/62771925.cms?from=mdr
Chapter 2
Lukebox
https://www.luxebook.in/fashion-designer-kresha-bajaj-shares-the-secret-behind-her-brands-massive-social-media-following/
Livemint
https://www.livemint.com/Consumer/uhBCZvMWKcE4vjs6c8ztHL/Celebrities-association-with-fashion-labels-see-a-surge-in-I.html
Chapter 3
Indiaretailing
https://www.indiaretailing.com/2017/06/18/fashion/5-trends-will-define-future-indian-apparel-industry/
Economic times
https://retail.economictimes.indiatimes.com/news/apparel-fashion/apparel/covid-19-impact-stylish-face-mask-is-the-new-focal-accessory-of-indias-top-fashion-brands/75639614)
Firstpost
https://www.firstpost.com/health/media-usage-during-covid-19-lockdown-indian-users-flock-to-fb-and-whatsapp-general-news-sites-see-numbers-rise-8242811.html
#fashion#nift#social media#instagram#pinterest#social media marketing#manish malhotra#covidー19#fashion industry
1 note
·
View note
Text
Enable hyper-v on vmware workstation 12 無料ダウンロード.「VMware」の上で「Hyper-V」を動かす
Enable hyper-v on vmware workstation 12 無料ダウンロード.VMware Workstation Player 12:ダウンロード、インストール、起動方法

VMware Workstation Player 12:インストール方法.Build VMware Workstation Pro 12 thinks Hyper-V is installed
Dec 11, · This is correct, because this virtual server FS01, is being hosted by a VMware vSphere (ESXi) Server. In this article, I’m going to take time out from writing a Basic VMware Article, and show you HOW TO: ENABLE and RUN Microsoft Hyper-V in a VMware vSphere Virtual Machine. You will find that running Microsoft Hyper-V virtual machines in a virtual Reviews: 9 Nov 28, · VMware Workstation 16 Player上で「Hyper-V」を動かす. という事で、今回は「VMware Workstation 16 Player上でHyper-Vを動かす」方法について書いてみたいと思います。. 私は「VirtualBoxメイン派」なので本当はVirtualBoxでやりたかったのですがそれは無理でした。. ・・・なの May 26, · Running Workstation on a Hyper-V Enabled Host. Running Workstation on a Hyper-V Enabled Host. The traditional implementation of Workstation Pro relies on direct access to specific hardware features of the x86 microprocessor. These features, generally called Intel VT or AMD-V, are also used by recent versions of Windows that support Hyper-V
Enable hyper-v on vmware workstation 12 無料ダウンロード.「VMware Workstation 12 Player」 がリリース!ダウンロードリンク及びインストール手順について | ネットセキュリティブログ
With the release of VMware Workstation/Player , we are very excited and proud to announce support for Windows hosts with Hyper-V mode enabled! As you may know, this is a joint project from both Microsoft and VMware. You can also check out Microsoft’s blog here. Since the introduction of Hyper-V, including Credential Guard and Device Apr 03, · Workstation 12 Pro version: build I simply created a typical VM by selecting "Hyper-V (unsupported)" as Guest OS system, others keep the default. After that, I opened VM settings, selected "Virtual Intel VT-x/EPT or AMD-V/RVI" and "Virtualize CPU performance counters" options, attached the win10 installation image May 20, · 以前「VMware Player」と呼ばれていた製品ですが、現在「 VMware Workstation Player 」という名称になっています。. VMware Workstation Player 12:ダウンロード方法. 無償(フリー)のVMware Workstation PlayerをダウンロードするためにはVmwareのこちらのWebサイトにアクセスします。
昨年8月26日に「VMware Player」の作成元である「VMware, Inc. ヴイエムウェア株式会社(本社:東京都港区、代表取締役社長:ジョン ロバートソン)は本日、業界をリードするPC向け仮想化ソフトウェアの最新バージョンであるVMware Workstation? インセンティブ プログラム クラウド コンピューティングのメリットをより身近に感じてもらうため、VMware Workstation 12 Pro のユーザに、最大6カ月間使用できる米ドル相当のVMware vCloud Airサービスクレジットを提供します。これはVMware vCloud Airの標準的な利用登録時に提供されるクレジットの2倍に相当します。. VMware Workstation 12 Player? 仮想マシンの管理に関心の高いVMware Workstationのユーザは、ライセンスをVMware HorizonR FLEX?
にアップグレードできます。ポリシーベースのコントロールを通じてローカルPC上で稼動する仮想デスクトップやアプリケーションを、中央からプロビジョニング/管理し、その安全性を向上できるため、VMware Horizon FLEXは、導入済みのVMware Workstationにさらなる管理機能を追加したいユーザにとって理想的なソリューションとなります。. VMware Workstation 10/11のユーザは、18,円からでVMware Workstation 12 Proにアップグレードいただけます。また、VMware Player 6 PlusとVMware Player 7 Proのユーザは、9,円からでWorkstation 12 Playerにアップグレードできます。.
そこで当記事は、年9月に「「VMware Workstation 12 Player」に関する導入手順」という記事テーマで記載した投稿となりますが、今回の投稿では、当記事を再投稿という形式で記載してまいりたいと思います。. 次に インストール という項目をクリックしてから、「VMware Workstation 12 Player」のインストールを開始してください。. 次に 「非営利目的でVMware Workstation 12 Playerを無償で利用する」 という項目にチェックを入れてから、赤線項目に任意のメールアドレスを入力して、さらに 続行 という項目をクリックします。.
そこで「VMware Workstation 12 Player」を使用するユーザーは、以下の「VMware Tools」をインストールする手順における過去記事を参照しながら、「VMware Workstation 12 Player」に「VMware Tools」をインストールすることを検討してください。. 今回の投稿で記載する記事以外の「VMware Workstation Player」の導入方法に関連する記事に興味がある方は、ぜひ一度以下の「VMware Workstation Player」の導入方法に関連する記事のまとめを参照してください。.
Please click here if you are not redirected within a few seconds. HOME All Post Category Security Win 10 Win 8. ソフトウェア 全般情報. 皆様、おはようございます。 本日の関東は雨模様の早朝となりました。 それでは今回の投稿にまいりましょう。 【スポンサーリンク】 はじめに 【目次】 はじめに 「VMware Workstation 12 Player」に関する導入手順 1、【ダウンロードリンク】 2、【インストール】 「VMware Workstation 12 Player」に「VMware Tools」をインストールする手順 あとがき.
0 notes
Text
Best Docker Bittorrent Client

Volumes and Paths

There are two common problems with Docker volumes: Paths that differ between the Radarr and download client container and paths that prevent fast moves and hard links. The first is a problem because the download client will report a download's path as /torrents/My.Movie.2018/, but in the Radarr container that might be at /downloads/My.Movie.2018/. The second is a performance issue and causes problems for seeding torrents. Both problems can be solved with well planned, consistent paths.
Most Docker images suggest paths like /movies and /downloads. This causes slow moves and doesn't allow hard links because they are considered two different file systems inside the container. Some also recommend paths for the download client container that are different from the Radarr container, like /torrents. The best solution is to use a single, common volume inside the containers, such as /data. Your Movies would be in /data/Movies, torrents in /data/downloads/torrents and/or usenet downloads in /data/downloads/usenet.
My Docker Hub — over an OpenVPN Still every now and 'luck' deploying one of / Qt that uses a VPN service have tried to deploy even of course if Jump to Test the VPN providers: — minimal image — To am setting up a a VPN service find a torrent client torrent client with WebUI use docker images for running on Jump be fail-secure: if the the.
A global team of 50+ experts have compiled this list of 7 Best Docker Tutorial, Certification, Training and Course available online for 2021.These resources will help you Learn Docker from scratch, and are suitable for beginners, intermediate learners as well as experts.
Learn how to install Docker on your machine, how to build a dockerfile, how to use the command line, how to use Docker with ASP.NET Core, and more in this comprehensive introduction. Use Winrar to Extract. And use a shorter path when extracting, such as C: drive. Docker container This container contains Is do this, other than torrent client with running Transmission torrent client a VPN provider. Simply setup docker containers Docker -proxy/ and add the of Transmission connected through an OpenVPN tunnel - preferred choice is Usenet.
If this advice is not followed, you may have to configure a Remote Path Mapping in the Radarr web UI (Settings › Download Clients).
Ownership and Permissions
Permissions and ownership of files is one of the most common problems for Radarr users, both inside and outside Docker. Most images have environment variables that can be used to override the default user, group and umask, you should decide this before setting up all of your containers. The recommendation is to use a common group for all related containers so that each container can use the shared group permissions to read and write files on the mounted volumes. Keep in mind that Radarr will need read and write to the download folders as well as the final folders. Minitool partition wizard alternative.
For a more detailed explanation of these issues, see The Best Docker Setup and Docker Guide wiki article.
Estimated reading time: 6 minutes
Docker Desktop for Windows is the Community version of Docker for Microsoft Windows.You can download Docker Desktop for Windows from Docker Hub.
This page contains information on installing Docker Desktop on Windows 10 Pro, Enterprise, and Education. If you are looking for information about installing Docker Desktop on Windows 10 Home, see Install Docker Desktop on Windows Home.
By downloading Docker Desktop, you agree to the terms of the Docker Software End User License Agreement and the Docker Data Processing Agreement.
What to know before you install
System Requirements
Docker Client Download
Windows 10 64-bit: Pro, Enterprise, or Education (Build 16299 or later).
For Windows 10 Home, see Install Docker Desktop on Windows Home.
Hyper-V and Containers Windows features must be enabled.
The following hardware prerequisites are required to successfully run ClientHyper-V on Windows 10:
64 bit processor with Second Level Address Translation (SLAT)
4GB system RAM
BIOS-level hardware virtualization support must be enabled in theBIOS settings. For more information, seeVirtualization.
Note: Docker supports Docker Desktop on Windows based on Microsoft’s support lifecycle for Windows 10 operating system. For more information, see the Windows lifecycle fact sheet.
What’s included in the installer
The Docker Desktop installation includes Docker Engine,Docker CLI client, Docker Compose,Notary,Kubernetes,and Credential Helper.
Containers and images created with Docker Desktop are shared between alluser accounts on machines where it is installed. This is because all Windowsaccounts use the same VM to build and run containers. Note that it is not possible to share containers and images between user accounts when using the Docker Desktop WSL 2 backend.
Nested virtualization scenarios, such as running Docker Desktop on aVMWare or Parallels instance might work, but there are no guarantees. Formore information, see Running Docker Desktop in nested virtualization scenarios.
About Windows containers
Looking for information on using Windows containers?
Switch between Windows and Linux containersdescribes how you can toggle between Linux and Windows containers in Docker Desktop and points you to the tutorial mentioned above.
Getting Started with Windows Containers (Lab)provides a tutorial on how to set up and run Windows containers on Windows 10, Windows Server 2016 and Windows Server 2019. It shows you how to use a MusicStore applicationwith Windows containers.
Docker Container Platform for Windows articles and blogposts on the Docker website.
Install Docker Desktop on Windows
Double-click Docker Desktop Installer.exe to run the installer.
If you haven’t already downloaded the installer (Docker Desktop Installer.exe), you can get it from Docker Hub. It typically downloads to your Downloads folder, or you can run it from the recent downloads bar at the bottom of your web browser.
When prompted, ensure the Enable Hyper-V Windows Features option is selected on the Configuration page.
Follow the instructions on the installation wizard to authorize the installer and proceed with the install.
When the installation is successful, click Close to complete the installation process.
If your admin account is different to your user account, you must add the user to the docker-users group. Run Computer Management as an administrator and navigate to Local Users and Groups > Groups > docker-users. Right-click to add the user to the group.Log out and log back in for the changes to take effect.
Start Docker Desktop
Docker Desktop does not start automatically after installation. To start Docker Desktop, search for Docker, and select Docker Desktop in the search results.
Ahnlab safe transaction uninstall mac. When the whale icon in the status bar stays steady, Docker Desktop is up-and-running, and is accessible from any terminal window.
If the whale icon is hidden in the Notifications area, click the up arrow on thetaskbar to show it. To learn more, see Docker Settings.
When the initialization is complete, Docker Desktop launches the onboarding tutorial. The tutorial includes a simple exercise to build an example Docker image, run it as a container, push and save the image to Docker Hub.
Congratulations! You are now successfully running Docker Desktop on Windows.
If you would like to rerun the tutorial, go to the Docker Desktop menu and select Learn.
Automatic updates
Docker Torrent Client
Starting with Docker Desktop 3.0.0, updates to Docker Desktop will be available automatically as delta updates from the previous version.
When an update is available, Docker Desktop automatically downloads it to your machine and displays an icon to indicate the availability of a newer version. All you need to do now is to click Update and restart from the Docker menu. This installs the latest update and restarts Docker Desktop for the changes to take effect.
Uninstall Docker Desktop
To uninstall Docker Desktop from your Windows machine:
From the Windows Start menu, select Settings > Apps > Apps & features.
Select Docker Desktop from the Apps & features list and then select Uninstall.
Click Uninstall to confirm your selection.
Note: Uninstalling Docker Desktop will destroy Docker containers and images local to the machine and remove the files generated by the application.
Save and restore data
You can use the following procedure to save and restore images and container data. For example, if you want to reset your VM disk:
Best Docker Bittorrent Client Ubuntu
Use docker save -o images.tar image1 (image2 ..) to save any images you want to keep. See save in the Docker Engine command line reference.
Use docker export -o myContainner1.tar container1 to export containers you want to keep. See export in the Docker Engine command line reference.
Uninstall the current version of Docker Desktop and install a different version, or reset your VM disk.
Use docker load -i images.tar to reload previously saved images. See load in the Docker Engine.
Use docker import -i myContainer1.tar to create a file system image corresponding to the previously exported containers. See import in the Docker Engine.
For information on how to back up and restore data volumes, see Backup, restore, or migrate data volumes.
Docker Client Java
Where to go next
Best Docker Bittorrent Client Installer
Getting started introduces Docker Desktop for Windows.
Get started with Docker is a tutorial that teaches you how todeploy a multi-service stack.
Troubleshooting describes common problems, workarounds, andhow to get support.
FAQs provides answers to frequently asked questions.
Release notes lists component updates, new features, and improvements associated with Docker Desktop releases.
Docker Client Update
windows, install, download, run, docker, local

0 notes
Text
Download Virtual Machine Mac Os X

VirtualBox is a general-purpose full virtualizer for x86 hardware, targeted at server, desktop and embedded use.For a thorough introduction to virtualization and VirtualBox.
Apple release every year a new operating system for there user. Indeed all of theme are currently much successful and attracted their user to be more satisfied. When Apple announces there OS for the public, firstly, they bring in developer mode. Every year Apple bringing huge changes to there operating system. Like macOS X El Capitan, macOS X Yosemite, macOS Sierra, macOS High Sierra, and macOS Mojave is out new and perfectly professionally made. With every feature of macOS Mojave, you are able to make your work easy. Such as after a longtime Apple experimented to bring the dark mode them into there OS. And finally, they did it and brought changes to there look too. Download macOS Mojave 10.14 ISO for VMware & VirtualBox.
Download Microsoft Outlook 2019 for Mac to manage your emails and stay up-to date with meetings and appointments. Microsoft Outlook for PC and Mac. Written by Microsoft Corporation. Category: Productivity Release date: 2019-11-14 Licence: Free Software version: 16.31 File size: 763.43 MB Compatibility: Windows 10/8.1/8/7/Vista and Mac OS X 10.13. If you looking on the internet an Microsoft Office 365 2019 v16.32 for Mac full version So, you come to the right place now a day shares with you an amazing application Microsoft Office 365 It includes Word, Excel, PowerPoint and the rest of tools of the office suite.Download Free Microsoft Office for Mac 2019 VL 16.32 DMG.It is a complete offline setup MS 2019 for Mac 16.32 Multilingual for. Features not yet available in the new Outlook for Mac. There are several features that are available in the current version of Outlook for Mac for Office 365 that aren't yet available in the new Outlook experience. S/MIME - Now available in Insider Fast version 16.43. Microsoft outlook for mac free download - Microsoft Outlook Express, Microsoft Outlook 2019, Microsoft Office 2011, and many more programs. Microsoft outlook 2011 for mac free download.
Every feature and functionality of the macOS Mojave is outstanding. For example, High Sierra allowed you to change the menu bar and dock to dark color, indeed that changes made the look a bit bright. But during the installation of macOS Mojave on your PC you can choose the dark mode. The included features in macOS Mojave are Dynamic Desktop, Desktop Stacks, Screenshots Markups, Screenshot Utility, Continuity Camera, iOS Apps on Mac, The APP Store, Finder, and others. Well, there’s is more to talk about macOS Mojave goodness’s, but the better way to access its features install it on your PC.

Installing macOS Mojave on Mac or PC – Hackintosh is pretty easy. First, we ready the required files, then creating a Bootable USB, and Post-Installation USB files. Gaining to install macOS Mojave on Windows PC is difficult and impossible. But again to the world developers era for there beneficial tools that they allow the opportunity to install macOS Mojave on Windows PC. In case, there is an easy way to install macOS Mojave on Windows PC. Like you can install macOS Mojave on VMware on Windows PC. Or more than that you can install macOS Mojave on VirtualBox on Windows PC.
On the Linux (Ubuntu.), open Terminal windows and CD to go to your Mac OS virtual machine directory. If you use the Windows operating system, open the CMD windows with Administrator privilege and CD to go to the Mac OS virtual machine directory.
Download a virtual machine. We currently package our virtual machines for four different virtualization software options: VMWare, Hyper-V, VirtualBox, and Parallels. Windows 10 Enterprise - 20 GB download. This VM will expire on 1/10/21.
In this document, I will guide you how to install Mac OS 10.11 on VMWare.
Related: Download macOS Mojave Image file for VMware & VirtualBox
Download macOS Mojave ISO For VMware & VirtualBox
When it comes to terms of installing macOS Mojave on VMware or VirtualBox. Using the macOS Mojave VMDK file or image file. As I have provided you the link in the above paragraph. Particularly, there are to main methods of installing macOS Mojave on VirtualBox and VMware. Before we were using for the purpose of installing macOS Mojave on VirtualBox or whether VMware using the exact VMDK “Virtual machine disk file”. But we prepared to install macOS Mojave in another way also.
And that is installing macOS Mojave on VirtualBox and VMware using the ISO file of Mojave. When it comes to VirtualBox, I think these tools of Virtualization are similar. We use ISO file of macOS Mojave for installing on VirtualBox on Windows PC too. We’ve downloaded and created the ISO file of macOS Mojave to install on Windows PC or somewhere else. All the required files of macOS Mojave is ready to download, there is no need again to access to Apple Mac Store for downloading macOS Mojave file. The macOS Mojave ISO file is downloaded, created, compressed, and uploaded on Google Drive. And I think if you follow the installation method that we did, you never face any kind of problem during the installation.
Download macOS Mojave ISO File
Also, you can download macOS Mojave 10.14 ISO file for VMware & VirtualBox latest version. The files are uploaded in MediaFire, which encrypted and compressed with WinRAR. And for the extracting the files you can use whether WinRAR or 7Zip. Indeed while extracting the file you will required the password, and you can find the password below the download links.
When the download is completed, you need to extract the compressed file. To do that use the WinRAR or 7Zip. Again if you faced any problem in the downloading case. Then check the below article on how to download macOS Mojave.
Again you can update macOS Mojave on VirtualBox or VMware on Windows to the latest version. There aren’t any differences between the updating method on VMware and VirtualBox. To that follow the bellow method.
That is the required file of macOS Mojave for installing macOS Mojave on VMware or VirtualBox. I think there aren’t any differences between the installation using the ISO file and VMDK file. But using the ISO file is a bit simple than the VMDK file.
That’s all about the macOS Mojave ISO file. Now everything is ready. let’s dig into the installation process of macOS Mojave on VMware & VirtualBox. To do that check the below links.
Install macOS Catalina on VMware on Windows PC (New Method)
One of the pretty easy ways of installing macOS Mojave on Windows PC is using VirtualBox. VirtualBox is also, a famous Virtualization tool. To do that installation of macOS Mojave on VirtualBox with a new method then check the below article.
Install macOS Mojave on VirtualBox on Windows PC (New Method)
That’s all about macOS Mojave ISO file, again if you think there is remaining something. Then feel free to share with us in the comment section. If the content was useful for you then your feedback is a big support for us. Also, don’t forget to share the post with your friends on social network platforms.
If your machine is part of the mainstream configuration, you can discard the traditional real native partition installation method, while the use of virtual machine method described in this article, not only greatly reduce the problems encountered difficult, but also in the use of Mac OS X to get the experience is excellent the. (This tutorial configuration needs: support hardware virtualization technology (Virtualization) of the CPU. Current mainstream Intel Core series and AMD Athlon series CPU virtualization technology is supported, the name was Intel VT-x and AMD-V.)

Description of the whole process
Preparatory work Installing VMware Crack VMware supports Mac OS X In VMware Install Mac OS X Finishing work late
Preparation
This tutorial method used by the virtual machine, provided that the machine's CPU must support hardware virtualization technology. Readers can be CPU-V or CPU-Z and other tools to test the result. Open CPU hardware virtualization technology can be turned on via the motherboard BIOS settings.
Download and install VMware Workstation VMware can go to the official website or on the ed2k network search download (recommended). Described here no longer compile.
Apple systems on Mac OS X installation disc image, use the dmg format of the original image. I recommend to search for ed2k network download (recommended), the keyword is 'Mac OS X Mountain Lion dmg' or 'Mac OS X Lion dmg'. Described here no longer compile.
Crack VMware Workstation supports Mac OS X Here we need to use the tool 'Workstation and Fusion Mac OS X Unlocker'
VMware Workstation and complete the installation after the restart, completely unpack Unlocker compressed package to the administrator mode windows/install.cmd. Jre java mac download.
Unlocker will automatically stop VMware services, backup VMware program files, program files crack VMware, restart the VMware service and a series of operations, and will automatically end the command line window.
After the break VMware has created a virtual machine system selection dialog:
Create Mac OS X, VMware virtual machines
After Unlocker crack, start VMware Workstation normally create a virtual machine, select 'Apple Mac OS X' (depending on the Mac OS installation disk in the system, select the corresponding version of the correct version, here I use a Mac OS X Mountain Lion, version 10.8 64-bit). Creation process has the following non-default configuration:
(1) in the processor options, select 'Number of cores per processor (each processor cores)' for the two, which can induce a VMware virtual machine automatically enables advanced hardware virtualization technology.
Download Virtual Machine Mac Os X Vmware
(2) after created, first click on the 'Edit virtual machine settings', the hardware's 'Floppy' delete option is enabled in the display 'Accelerate 3D graphics'.
(3) In Virtual machine configuration, in the Advanced Settings, set the priority of the input capture 'high', and check 'Disable memory page trimming.
With a text editor (such as Notepad) to edit the virtual machine files (where the author is E:Program Files(x86)Virtual_MachinesMac OS XMac OS X.vmx), add a line at the end of the file:
This operation is used to disable the VMware virtual machine is placed on your hard disk memory mirroring prevents the virtual machine hard disk read and write operation occurs during the busy horrors.
Start the VMware virtual machine and install Mac OS X
Edit the virtual machine configuration 'CD / DVD' option in the 'Use ISO image file' at the choice of our Mac OS X installation disc image. (Please select the browse file dialog box when the file type, select 'All Files (*. *)', You can see the file name suffix for the dmg image file.) Confirmation is complete, start the VMware virtual machine.
Start the virtual machine, the virtual machine default boot from the CD, the Apple Logo appears after officially came to Mac OS X installation interface.
In the 'Mac OS X Utilities' select 'Disk Utility', select the first hard drive on the left and on the right select 'Erase' (the 'Format' select 'Mac OS X Extended (Journaled)'), Click the 'Erase' button to format the current drive.
Download Virtual Machine Mac Os X 10 13 Download

Virtualbox
After formatting the hard disk partition, back to 'Mac OS X Utilities' and click 'Install Mac OS X', enter the installation process.
Virtual Machine Mac Os
Completed in a VMware virtual machine after installing Mac OS X, the first thing of course is to install VMware Tools. VMware Tools includes the VMware virtual machine 'hardware' drive, the virtual machine and the host communication between functional support.
Download Virtual Machine Mac Os X Lion
Tools used herein Attachments Download

0 notes
Text
Online Server Administration Training
The Server Administrator has the full control of a server. The main role of a server administrator is to preform various things related to server or servers.
Roles of a Server Administrator
configuration
management
improve servers
This ensures perfectly working and cost efficiency of the server.
The Server Administrator will help with managing the physical security, uprightness, and well being of the server or data centres.
Salary of a Server Administrator:- Depends on the company and size of the server infrastructure and the experience level
Starting Range Salary = 15k / month
Mid Range Salary = 35k - 50k / month
Advance Range Salary = Starting from 90k / month
How this program will help you?
This Certification Program will help with laying preparation towards a world-class Server Administrator and Engineer, this program is both an journey and a destination. A way to become skilled IT professional and demonstrate your expertise to the world. It helps you to gain skills and proficiency in the latest Server technologies and solutions.
Our Mission
Provide enhance recognition and career development.
Prove commitment to growing IT skills.
Demonstrate job readiness and performance.
Why Us?
Get trained by Server Administrators who has years of experience.
100% practical training
Each trainee will have access to his/her server 24/7.
We develop troubleshooting skills on our own production servers.
Job Placement assistance and interview preparation.
Training Modules
Module 1
Introduction and basics of Linux
Linux administration - Beginner
Linux administration - Networking
Linux administration - Advanced
Linux firewall configuration
Module 2
DNS Server installation, configuration & administration - Linux
FTP Server installation, configuration & administration - Linux
Web Server installation, configuration & administration - Linux
PHP installation, configuration & administration - Linux
Database Server (MySQL) installation, configuration & administration - Linux
Email Server installation, configuration & administration - Linux
Module 3
Introduction and basics of Windows Servers
Windows Server administration - Beginner
Windows Server administration - Networking
Windows Server firewall configuration
Module 4
DNS Server installation, configuration & administration - Windows Server
Web Server installation, configuration & administration - Windows Server
PHP installation, configuration & administration - Windows Server
ASP. Net installation, configuration & administration - Windows Server
Module 5
Email Server installation, configuration & administration - Windows Server
FTP Server installation, configuration & administration - Windows Server
Database Server (MySQL) installation, configuration & administration - Windows Server
Microsoft SQL Server installation, configuration & administration - Windows Server
Module 6
Introduction to Web hosting & Control Panel
Linux cPanel installation, configuration & administration
Linux Virtualmin installation, configuration & administration
Windows WebsitePanel installation, configuration & administration
Windows Plesk installation, configuration & administration
Installation and configuration of PHP/Asp.net web applications
(Joomla, WordPress, DotNetNuke etc.)
Module 7
Linux Server backup & disaster recovery strategies
Linux MySQL databases backup & disaster recovery strategies
Windows Server backup & disaster recovery strategies
Windows MS SQL databases backup & disaster recovery strategies
Windows MySQL databases backup & disaster recovery strategies
Module 8
Linux hacking - admin password break/reset & recovery
Linux hacking - access data (files/folders) on locked system
Windows hacking - admin password break/reset & recovery
Windows hacking - access data (files/folders) on locked system
Linux Server - recover damaged/unbootable system
Windows Server - recover damaged/non booting system
Module 9
Introduction to Server Security, hacking attacks & techniques
Hacking test website's to understand how hackers work
Securing Linux Servers
Linux tools and techniques to fight against hackers
Securing Windows Server
Windows tools and techniques to fight against hackers
Implementing Web application firewall on servers to mitigate common hack attacks
Module 10
Introduction to SPAM emails & Spammers
Install configure & manage spam filter for Mail Servers
Tweaking and optimization of Web server, PHP & MySQL Server
Introduction to DNS clustering
Install, configure & manage DNS cluster
Module 11
Introduction to Intelligent Platform Management Interface (IPMI)
Intelligent Platform Management Interface (IPMI) configuration & management
Troubleshooting OS problem using IPMI
Remote Operating System installation using IPMI
Remote troubleshooting Operating System, backup and file system management using IPMI
Module 12
Introduction to cloud computing & virtualization
Virtualization/cloud - install, configure & manage Linux KVM
Virtualization/cloud - install, configure & manage Microsoft Windows Hyper-V
Virtualization/cloud - install, configure & manage VMware vSphere - ESXi
Cloud computing - install, configure & manage private cloud infrastructure (VMware)
Cloud computing - install, configure & manage private cloud infrastructure
(RHEV/OVIRT)
Virtualisation / cloud infrastructure backup & disaster recovery strategies
Module 13
Improving troubleshooting skills
Learn how to analyse system logs to troubleshoot issues
How to use Google to troubleshoot issues
Troubleshooting common server side issues
Want to know more about the course or when new batch is starting?
Reach us at 9806532911 or 7987168352
1 note
·
View note
Text
The Rise of the Virtual Machines

Criminals are among the most advanced users of modern technology. They learned how to hide information in their smartphones and how to encrypt their laptops. They communicate via secure channels. Their passwords never leak, and they do their best to leave no traces. Forensic investigators encounter new challenges every other day. In this article, we will discuss yet another tool used by the criminals to cover their traces: the encrypted virtual machine. Introduction to virtual machines Virtual machines use a portable, hardware-independent environment to perform essentially the same tasks as the actual computer. User activities performed inside a virtual machine remain leave trails mostly in the VM image files and not on the host computer, limiting the number and severity of traces in a natural way. Virtual machine analysis becomes an important factor when performing digital investigations. Some of the most popular virtual machines include VirtualBox, Parallels, and VMWare. While Microsoft offers Hyper-V, the tool to create virtual machines on Windows 10, Hyper-V offers limited encryption options, requiring Windows Server as a host OS. For this and other reasons, Hyper-V is rarely picked by the criminals. Virtual machine as a criminal tool Many types of virtual machines used in the criminal world can be securely encrypted. Read the full article
0 notes
Text
Watch "Introduction to hyper v on windows 10 | Introduction to hyper-v on windows 10" on YouTube
Watch “Introduction to hyper v on windows 10 | Introduction to hyper-v on windows 10” on YouTube
View On WordPress
#Hyper-V hyperv VirtualMachine VirtualizationWindows10 Introductionhyperv hypervisor windows10 virtualmachine virtualizationserver#alternative to virtual box#hyper v switch#hyper v windows 10 pro#introduction to hyper v on windows 10#Lesson one introduction to hyper#Microsoft Hyper V - Introduction#Oracle VM VirtualBox#virtual machine windows 10#Virtualisation#Virtualization video tutorial#virtulisation#vM#windows hyperv#windows hypervisor
0 notes
Link
Introduction
One of the common struggles in a large data collection environments, like collecting the SQL audit trails is the low storage space event. With the mechanisms provided by the ApexSQL Audit tool and with some alternative methods using PowerShell automation, these issues can be prevented or resolved.
This article explains what built-in methods for low storage space events ApexSQL Audit can offer and how to resolve critical situations where the storage space situation has to be resolved unattended.
Temporary files
One of the methods to manage and distribute necessary storage during SQL auditing is to plan and set the location for temporary file storage. These files represent collected SQL audit data from an audited instance that is queued to be processed and imported in the central repository, and it is set per audited SQL Server instance. In case the low storage space event occurs for the partition where temporary files are set, some auditing data can be lost.
When a new instance is added for auditing, the dialogue that defines the connection to that instance will have the option to set the temporary files location. This can be a location with some storage space reserves and/or low storage consumption in general.
This dialogue will appear when a new audited SQL Server instance is added in the Configure view, but it can be invoked by selecting an existing audited instance and clicking the Edit button. In there, the temporary files location can be changed:
Low storage space for the central instance
As mentioned, collected SQL audit data is stored in a central repository database and can consume a lot of space through time. The archiving method allows emptying the central repository database by creating an archive database from the repository and creating a new repository database. Still, this archive is going to be attached to the same SQL Server instance as the central repository database, so the accumulation of store date will still continue.
For critical situations when a low storage space event occurs, on the machine where the central repository database is hosted, ApexSQL Audit has built-in alerts, a notification system to inform an operator by email that the event occurred. Setting this alert to work properly will require defining the email recipient as well as some general settings.
To do that, click on the Manage button in the Alerting section of the main menu, then select the Disk space alert for central repository host alert item, and then Edit to open configuration wizard for this alert:
The first step of the wizard is where the email content is defined:
When email content is defined, the following of the wizard will require a definition for remaining storage space before alert triggers. This is where the option to stop collecting auditing data can also be set if the event occurs:
The following step defines when the storage space monitoring should start and what would be the checkup intervals:
The next step is where the alerting notification can be turned on to be recorded in the Windows event logs and sent to the selected email contact profile:
The contact profile is configured in the Email recipient list tab of the main application Options window:
The final wizard step shows a summary of the alerting configuration, which can be confirmed with the Finish button:
If an SQL audit manager receives this notification, some actions can be performed to remedy the situation. One of the possible actions would be to detach some of the archived central repository databases from the hosting SQL Server and migrate the database image (the associated .mdf and .ldf files) to another storage then reattaching the database to that or another SQL Server instance:
For the changes like that, it would be necessary to check and update reporting data sources from the Reporting tab of the application main Options window. If the archive is relocated to another SQL Server instance, that instance should be targeted and the archive database selected:
Low storage space handling with PowerShell automation
It is possible that a low storage space situation occurs and left unattended for a longer period of time. At this point, there will be a risk that SQL audit data collection will not be working. In cases that this situation occurs on a virtual machine, it is possible to automate the process of resolving the low storage space situation by expanding the virtual drive through PowerShell.
This automation setup starts by setting up the scheduled task to be triggered on the Windows event ID that identifies low storage space events. This is categorized as the System event with ID 2013:
Setting the scheduled task is performed as usual. Use the Create task option in the Windows task scheduler, and set the trigger to activate it on the System event from the Log drop-down list and type in number 2013 in the Event ID field. It would be advisable to set a delay for this task execution to leave some time for a manual intervention:
As for the action that is going to be triggered, go to the Actions tab and create New action defined as Start s program and insert the path to the PowerShell automation script file which will be created:
The location for the PowerShell automation script that will be executed will have to be some network shared folder or a network drive. Resizing a virtual drive usually requires shut down of a virtual machine, this applies to Azure virtual machines, until Microsoft introduces this feature to Azure, and Hyper-V machines unless their storage is hosted with a SCSI controller, in that case resizing can be done “live”. This is not a popular measure to shut down the working machine, but in these critical events, when attendance is not expected for a longer time, it would be beneficial compared to full machine operation halt due to lack of storage space.
This is why the resizing operation has to be performed from a remote location.
The single requirement for the PowerShell automation scripts to work with the Azure environment would be the Azure PowerShell module that can be installed by executing the command Install-Module -Name Az from the PowerShell console, and for the Hyper-V PowerShell automation management the Hyper-V module for Windows PowerShell will have to be installed from the Windows Features location:
Azure script
At first, the connection to Azure resources will have to be established from within the script. The commands will have to be created that the connection is established automatically, without prompting for credentials:
#Read the username for Azure logon $Username = "Domain\User" #Read the encrypted password for Azure logon stored in a text file $EncryptedPass = Get-Content -Path "C:\Credentials\AzurePassword.txt" #Convert encrypted password to usable secured string $Pass=[Runtime.InteropServices.Marshal]::PtrToStringAuto([Runtime.InteropServices.Marshal]::SecureStringToBSTR((ConvertTo-SecureString $EncryptedSCPass))) #Create credentials object with username and password to be used for connection $Creds = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $Username, $Pass #Connect to Azure services using created credentials object Connect-AzAccount -Credential $creds
The password part (where the password is read from a saved file) can be resolved using instructions from the following article:
PowerShell encrypt password techniques for SQL Server
With established connection, the script can continue with following commands that will manipulate the Azure virtual machine:
#Select focus to desired Azure subscription where resources are hosted Select-AzSubscription -SubscriptionName 'Name for subscription where VM resource is located' #Define the resource group name where VM is located $ResourceGroupName = 'DEVOPS' #Define the name of the VM where SQL audit central repository database is located $VirtualMachineName = 'Win-10' #Read properties of the VM and store them in an object $vm = Get-AzVM -ResourceGroupName $ResourceGroupName -Name $VirtualMachineName #Stop the target VM, use the Force parameter to prevent prompting for confirmation Stop-AzVM -ResourceGroupName $ResourceGroupName -Name $VirtualMachineName -force #Change the value in the VM object for the disk size property attached to VM $vm.StorageProfile.OSDisk.DiskSizeGB = 150 #Update VM definition with new disk size value Update-AzVM -ResourceGroupName $ResourceGroupName -VM $vm #Start the VM Start-AzVM -ResourceGroupName $ResourceGroupName -Name $VirtualMachineName
Previous commands will be used to handle unmanaged disks. If a virtual machine profile includes managed disks, then the commands will have to address directly disk properties instead of virtual machine properties. The commands after the stopping command would be:
#Read properties of the Disk from the VM properties and store them in an object $disk= Get-AzDisk -ResourceGroupName $ResourceGroupName -DiskName $vm.StorageProfile.OsDisk.Name #Set the value for the DiskSizeGB property of the Disk object $disk.DiskSizeGB = 150 #Update Disk definition with new disk size value Update-AzDisk -ResourceGroupName $ResourceGroupName -Disk $disk -DiskName $disk.Name #Start the VM Start-AzVM -ResourceGroupName $ResourceGroupName -Name $VirtualMachineName
Analog to this, a drive attached to Hyper-V machine can be extended; this time credentials would not be necessary as it is considered in a local network:
#Stop the VM machine with a given name Stop-VM -Name 'Win 10' #Red the properties of the virtual drive attached to the virtual machine $disk = Get-VHD -Path 'C:\Users\MRancic\Desktop\converted\win 10.vhdx' #Read the velue for disk size property, increment it by desired amount and store the value in object $disksize = $disk.Size + 20gb #Set the new value, stored in the $DiskSize object, for the virtual disk Resize-VHD -Path 'C:\Users\MRancic\Desktop\converted\win 10.vhdx' -SizeBytes $disksize #Start the VM machine with a given name Start-VM -Name 'Win 10'
The resizing operation is not done here; now we have unallocated space that the partition will be expanded with. This means that another scheduled task should be set triggered at startup:
The action will be to execute another PowerShell automation script which will check if there is contiguous unallocated space present and if so, to expand partition with that space:
#Define the drive letter that will be checked for expansion $Drive2Expand='C' #Read the amount of available unallocated space and store the information of current disk size $CurrentDisk = Get-Volume | Where DriveLetter -eq $Drive2Expand | ForEach-Object { $Size = Get-PartitionSupportedSize -DriveLetter $_.DriveLetter If ($Size.SizeMax -gt $_.Size) { $_ } } #Check if current disk size is smaller than possible max size, with offset of 10000 bytes to avoid cases where some unallocated space is left smaller than the cluster size if ($Size.SizeMax -gt $CurrentDisk.Size+10000) { #Get the partition number for chosen drive letter $PartitionNum=(Get-Partition -DriveLetter $Drive2Expand) #Get disk number of default hyper-v boot drive but change if expanding a secondary or non-boot drive $VirtDiskNum=(Get-Disk | Where IsBoot -eq Yes ) #Expand drive C using all unallocated space available Resize-Partition -PartitionNumber $PartitionNum.PartitionNumber -Size $Size.SizeMax -DiskNumber $VirtDiskNum.number }
As stated before, this script will perform the action only if unallocated space is detected.
This PowerShell automation solution, along with other application built-in methods, can prevent critical situations where SQL audit operations might come to a halt because of low storage space events.
0 notes
Text
Role of VATS in Ectopic Mediastinal Parathyroid Tumor- Juniper publishers
Introduction
In 1849, Sir Richard Owen, provided the first accurate description of the normal parathyroid gland after autopsy examination of an Indian rhinoceros. However, Ivar Sandstrom suggested these glands being named Glandulae parathyroideae. The first successful parathyroidectomy was performed in 1925 by Felix Mandl. It was Edward Churchill who identified first time the ectopic parathyroid adenoma substernally on his one of the patients in 1926. Embryologically, the superior parathyroid glands are derived from the 4th branchial pouch while the inferior parathyroids are derived from 3rd branchial pouch [1]. However, true ectopic superior parathyroid glands are rare, but may be found in the middle or posterior mediastinum or in the aorto-pulmonary window [2].
Primary hyperparathyroidism is a common disorder affecting 100,000 individuals annually in US. It occurs in 0.1% to 0.3% of the general population and is more common in women (1:500) than in men (1:2000). It is characterized by increased parathyroid cell proliferation and PTH secretion that is independent of serum calcium levels. Though the exact etiology of PHPT is unknown, although exposure to low-dose therapeutic ionizing radiations, familial predisposition and genetic factors account for some cases.
We have done over 400 cases of parathyroid surgeries in last 10 years in our department but only 4 patients presented with ectopic parathyroid disease [3] cases were in anterior mediastinum and only 1 case in posterior mediastinum). We are showing the management of ectopic parathyroid tumor in posterior mediastinum and role of VATS, its benefits over standard open thoracotomy in managing ectopic parathyroid tumor.
Go to
Subjects And Methods
63 year old lady presented with generalized bony pains, history of recurrent renal stones. She got operated twice, one for right renal stones with PCNL in 2011 (outside) and another dynamic hip screw for neck of femur fracture in 2014. During evaluation, her vitas were stable with essentially normal systemic examination. On local examination of neck, no palpable neck swelling was evident. On further evaluation by biochemical studies, she was found to be hypercalcemic with serum calcium levels of 13mg/dl with decreased serum phosphate and elevated 24 hour urinary calcium concentrations her serum PTH levels were 320ng/ml (high).
On radiological evaluation, her DEXA scan showed T score of -3.0 at the region of distal radius bone. Her ultrasound whole abdomen revealed non-obstructing 2mm stone right renal upper calyx. Ultrasound neck showed no abnormality. Sestimibitechnetium 99m scan revealed uptake over right mediastinal region (Figure 1). MRI neck and chest revealed 2.5cmx2.0cm oval shaped hyperintense lesion in the right paratracheal region in postero superior mediastinum (Figure 2). With the diagnosis of primary hyperparathyroidism with ectopic mediastinal parathyroid adenoma, she was optimized for surgery. She underwent Video- assisted thoracoscopic surgical approach.3 ports were made. 2 working ports of 5mm size were made on right anterior axillary and midclavicular line and one 10mm camera port was made midway between two 5mm ports. Her operative findings revealed an oval shaped 2.5cmx2cm hyper vascular lesion abutting right posterlateral wall of SVC. The tumor was excised using Harmonic scalpel energy device. Intraoperative IOPTH levels were sent during surgery and at 10 minutes after the excision of tumor with significant drop (>50%) in serum PTH post excision values. Hemostasis was achieved. Ports were closed with skin stapler after placing a intercostal drain from 10mm port site (Figure 3 & 4).
She developed hypocalcemia on post operative day 1 and was managed with i/v calcium for 2 days and stabilized later with oral calcium and vitamin D supplements in the follow up period. She was discharged on postoperative day 4.
Go to
Results
Histopathology report revealed parathyroid adenoma. During her first postoperative follow up after 2 weeks of surgery, her serum calcium levels were 8mg/dl and returned to normal activities within a week without pulmonary complications. At present she is on regular follow up and is doing fine.
Go to
Discussion
Primary hyperparathyroidism with ectopic parathyroid tumor being a rare entity. In the background of clinical symptoms and biochemical studies suggestive of hyperparathyroidism with no clinically palpable neck mass, high suspicion of ectopic parathyroid tumor should be kept in mind. Sestimibi-technetium 99m scan allows planar and SPECT imaging to identify ectopic parathyroid tumor. Also SPECT scan can indicate whether an adenoma is located in anterior or posterior mediastinum, thus enabling the surgeon to modify the operative approach accordingly. Though CT and MRI scans are less sensitive than sestimibi scans but are helpful in localizing large paraesophageal and mediastinal glands. The intraoperative PTH levels fall of >50% after 10mins. of gland excision is considered reliable test [3]. Thoracic surgical approaches have changed over recent years with advancements in minimally invasive surgery. As surgeon trained in advanced minimally invasive techniques can now perform pleural based, pulmonary and mediastinal procedures through multiple thoracoscopic ports without the need for a substantial, rib spreading incision. For ectopic mediastinal parathyroid tumor excision, either open sternotomy or VATS approach can be undertaken. Subjective measures of quality of life after VATS such as pain and perceived functional recovery, consistently and reproducibly favor VATS over thoracotomy [4]. Objective measures such as functional status as measured by 6min walk, return to work and daily activities also favor VATS over thoracotomy.
Finally recovery of respiratory function occur earlier in VATS patients [4]. When VATS is not possible, an open approach mostly posterlateral thoracotomy is used to gain access to the in trathoracic space for operations in the posterior mediastinum, pulmonary and oesophageal resections [5].
For more Journals in Juniper Publishers please click on https://juniperpublishers.com/journals.php
For more articles in Journal of Thyroid Research please click on: https://juniperpublishers.com/jetr/index.php
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Experts observed an increase of the malware spreading using less-known archive types as dropper,in particular ISO image.Delphi wrapper makes analysis harder
Introduction
In the last period, we observed an increase of the malware spreading using less-known archive types as an initial dropper, in particular, ISO image.
The spread of threats exploiting ISO image to hide themselves is helped by the Windows functionality, introduced since Windows 8, which allows the user to easily mount this file type through a double-click on it.
Recently, our monitoring operations discovered an interesting attack wave leveraging this technique, especially due to the particular impersonification the attacker was trying: he/they was mimicking an important Italian Manufacturing company.
Technical Analysis
Figure 1. Phishing email content
The phishing email (Figure 1) has a well-designed body containing the enterprise logo and references about the impersonated company: its international reputation has been abused by attackers to lure the victim to open up the embedded attachment.
Surely the presence of an ISO file as attachment is suspicious, but for an unaware user it could go unnoticed, also thanks to the new Windows versions which natively support the filetype.
The Loader
Extracting the content of the ISO image, we encounter an EXE file named “po-ima0948436.exe”. From the first retrieved information, in particular the “BobSoft Mini Delphi” signature, it seems to be packed with a well-known Delphi packer (already studied by other popular firms). According to FireEye this packer is already used by different malware family, like Pony, IRStealer, Nanocore, Netwire, Remcos, nJRAT. Moreover, in our previous report we have already studied the Delphi wrapper, this time applied to a Nanocore variant.
Figure 2. Evidence of the Delphi wrapper
As expected, the malicious payload is stored in the resource section in encrypted way (probably using a simple XOR-encryption). This is one of the main features of the Delphi packer.
Figure 3. Encrypted payload, stored in Resource section
Rather than studying the payload extraction mechanism, we focused on the huge number of checks to detect the lab environment and, consequently, to make the analysis harder. The evasion tricks are surely part of initial Delphi packer; it probably was generated using a specific factory which allows the attacker to customize the features will be added to its weapon.
Once executed, the malware obviously kills itself detecting the analysis machine, so we are going to investigate what are the tricks employed to stop us. Using our custom tool, we are able to extract information about the high-level techniques fielded by the malware writer to evade the analysis.
Figure 4. High-level evasion techniques
The first trick exploits a well-known Windows API call, “IsDebuggerPresent” to check if the process is executed in debugging mode. Bypass this control is quite simple: using a debugger we can modify the return value of the API call, hijacking the malware control flow.
Figure 5. IsDebuggerPresent API call
Immediately after the first trick, the malware shows another technique to identify the fake environment, monitoring the cursor movements. The cursor movements, indeed, represent the presence of a user operating with the system. So, the malware can identify if it is executed in a sandbox evaluating the different position of the cursor in periodic time intervals. This can be done through a finite loop in which the process check the position using the “GetCursorPos” API call.
Figure 5. Check against the cursor movements
After that, the malware retrieves the list of all active processes. This list will be used later to identify the presence of programs belonging to analysis environment. The most popular strategy to obtain the processes list is to use the “CreateToolhelp32Snapshot” Windows function. The malware needs to navigate the list in order to create a buffer with the processes’ executable paths only (“svchost.exe”, “services.exe” etc.). So, it must invoke the “Process32First” and “Process32Next” API calls, enter in the PROCESSENTRY32 structure and extract the “szExeFile” field, containing the executable path name.
Figure 6. API calls to obtain the processes list
The information about the processes are stored to be processed in a second moment. At this point, the malware exhibits another evasion technique, but more advanced than the previous ones. Using the CPUID instruction, it tries to extract information about the processor and its features.
According to VMware specifications “Intel and AMD have reserved CPUID leaves 0x40000000 – 0x400000FF for software use. Hypervisors can use these leaves to provide an interface to pass information from the hypervisor to the guest operating system running inside a virtual machine. […] VMware defines the 0x40000000 leaf as the hypervisor CPUID information leaf”. So, calling the instruction with the 0x40000000 parameter (in EAX register), the query result is the “Hypervisor Brand” string, split into three different registers: ECX, EDX and EBX (shown in Figure 7).
Figure 7. Result of CPUID instruction invocation
As shown in the above figure, the result string is reversed: the malware needs to manipulate it to obtain the right information “VMwareVMware” (Figure 8).
Figure 8. String reporting the hypervisor brand
Using this information, the malware is able to check if it is executed on a virtualized environment comparing the string with the embedded ones:
XenVMMXenVMM (Xen VM)
prl hyperv (Parallels)
Microsoft Hv (Microsoft Hyper-V )
KVMKVMKVM (KVM)
VBoxVBoxVBox (VirtualBox)
VMwareVMware (VMware)
Figure 9. Embedded string used during the hypervisor check
Bypassed this check, the malware knows to be in a non-virtualized environment but it is not yet the time to pull out its malicious behavior! At this point, in fact, it reloads the old processes list, retrieved in a previous phase, to compare its entries with the hardcoded names belonging to programs used in malware analysis, like:
procmon.exe
ollydbg.exe
procexp.exe
windbg.exe
Figure 10. Check against malware analysis tools
The same is done with components belonging to anti-malware products, in particular Avast and AVG. The hardcoded components names are:
avastsvc.exe
avastui.exe
avgsvc.exe
avgui.exe
Figure 11. Check against anti-malware software components
The last check consists in the identification of defined strings, related to malware analysis environment, with the absolute path in which the initial EXE is located. If the path contains words like “sandbox”, “malware”, “sample”, “virus” and others, the execution flow terminates.
Figure 12. Check against suspicious strings in path
If all the checks are successful, the malware can show its malicious behavior. It creates a child process containing the same instructions of its parent, so it repeats all the checks just executed, but it has the only purpose of injecting the final payload in a new “iexplore.exe” process.
Figure 13. Active processes
Analyzing the process, it is possible to identify a suspicious thread starting from 0x00000000address. Probably the technique used to inject malicious code in the legit one is based on “CreateRemoteThread”, with which the malware is able to allocate memory in the legit process memory space, fill it with malicious instructions and force the victim process to start the execution of the new thread.
Figure 14. Injected thread
The Payload
The final payload is nothing more XpertRAT, a well-known Remote Administration Tool. When executed, it writes a copy of itself in a hidden folder named %AppData%Roaming{GUID},setting the persistence writing the HKCUSoftwareMicrosoftWindowsCurrentVersionRun{GUID} with the location of the EXE just created.
Figure 15. Malware’s artifacts
In the below figure, it is possible to see the written registry key pointing to the executable to start at the next logons.
Figure 16. Malware persistence through registry key
In the same folder, there is a file named “ut” which is used by the malware as buffer to contain the exfiltrated data in “keylogging” mode, before sending it to the server.
So, the RAT tries to establish a connection to its C2, hosted at “thisurl.doesntexist[.]com”, waiting for new commands to execute on the victim machine.
Figure 17. Malware attempt to communicate
Unfortunately, the server seems to be down at the analysis time, so we can only inspect the network flow using a fake net. As shown in the following figure, the malware sends a TCP stream containing some parameters used at server-side to identify the client that tries to establish the connection.
Figure 18. Malware’s network traffic
Conclusion
Finally, the analyzed sample is a classic Remote Administration Tool which has a long list of capabilities, such as keylogging, remote desktop, command execution and other exfiltration abilities.
However, the interesting part of the analysis is surely the initial Delphi wrapper, which is full of advanced tricks to make the analysis harder. As mentioned before, this packer surely derives from some kind of factory which allows the attacker to choose the capabilities he wants. We, in fact, intercepted many other infections based on the same Delphi structure, but with different features in terms of evasion and encryption, as evidence of the possibility of customize it.
Technical details, including IoCs and Yara Rules, are available in the analysis published in the Yoroi blog.
https://blog.yoroi.company/research/spotting-rats-tales-from-a-criminal-attack/
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – ISO image, Delphi wrapper)
The post Spotting RATs: Delphi wrapper makes the analysis harder appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Spotting RATs: Delphi wrapper makes the analysis harder Original Post from Security Affairs Author: Pierluigi Paganini Experts observed an increase of the malware spreading using less-known archive types as dropper,in particular ISO image.Delphi wrapper makes analysis harder…
0 notes
Text
10 Free Courses to Learn Docker for Programmers
Here is my list of some of the best, free courses to learn Docker in 2019. They are an excellent resource for both beginners and experienced developers.
1. Docker Essentials
If you have heard all the buzz around Docker and containers and are wondering what they are and how to get started using them, then this course is for you.
In this course, you will learn how to install Docker, configure it for use on your local system, clone and work with Docker images, instantiate containers, mount host volumes, redirect ports and understand how to manage images and containers.
After completing the course you should be able to implement containers in your projects/environment while having a firm understanding of their use cases, both for and against.
In short, one of the best course for developers and DevOps Engineers who want to learn basics, like what Docker containers are and how to use them in their environment.
2. Understanding Docker and using it for Selenium Automation
This is another good course to learn and understand the basics of Docker while automating Selenium test cases for your project.
The course is specially designed for DevOps engineers, automation guys, testers, and developers.
The course is divided into three main parts: Introduction of Docker, Docker Compose, and Selenium Grid with Docker.
The three sections are independent of each other and you can learn than in parallel or switch back and forth.
3. Docker for Beginners
This is one of the best sources to learn the big picture of Docker and containerization. If you know a little bit about virtualization, networking, and cloud computing, then you can join this course.
It provides a good introduction to current software development trend and what problems Docker solves.
In short, this is a good course for Software and IT architects, Programmers, IT administrator and anyone who want to understand the role of Docker in current world application development.
4. Containers 101
Docker and containers are a whole new way of developing and delivering applications and IT infrastructure.
This course will cover Docker and containers, container registries, container orchestration, understand if this will work for the enterprise, and how to prepare yourself for it.
In short, a good course for anyone who wants to get up to speed with containers and Docker.
5. Docker Swarm: Native Docker Clustering
Managing Docker at scale is the next challenge facing IT. This course, Docker Swarm: Native Docker Clustering will teach you everything you need to know about Docker Swarm, the native solution for managing Docker environments at scale.
It’s a good course for Developers, Networking Teams, DevOps Engineers, and Networking infrastructure teams.
This was a paid course earlier on Udemy, but it’s free for a limited time. Join this course before it becomes paid again.
6. Docker Course Made for Developers
Whether or not you’re a Developer, anyone who works with code or servers will boost their productivity with Docker’s open app-building platform.
In this course, you will learn how to use the Docker products, like Docker Toolbox, Docker Client, Docker Machine, Docker Compose, Kinematic, and Docker Cloud.
You will also learn how to work with images and containers, how to get your project running, and how to push it to the cloud, among other important lessons.
7. Docker on Windows 10 and Server 2016
If you are thinking to learn how to use Docker on Windows 10 and Windows Server 2016 then this is the right course for you.
In this course, you will understand what Docker On Windows is all about and how Docker on Windows is the same as Linux Containers.
You will also learn Hyper-V, namespace isolation and server containers in depth.
8. Deploying Containerized Applications Technical Overview
Docker has become the de facto standard for defining and running containers in the Linux operating system. Kubernetes is Red Hat’s choice for container orchestration.
OpenShift, built upon Docker, Kubernetes, and other open source software projects, provides Platform-as-a-Service (PaaS) for the ultimate in deploying applications within containers.
This is an Official Red Hat course about containers using Docker running on Red Hat Enterprise Linux.
In this course, Jim Rigsbee, a curriculum architect for Red Hat Training, will introduce you to container technology using Docker running on Red Hat Enterprise Linux
9. Docker Deep Dive
As the title suggests this is a great course to learn Docker in depth. It provides a good experience for core Docker technologies, including the Docker Engine, Images, Containers, Registries, Networking, Storage, and more.
You will also learn theory and all concepts are clearly demonstrated on the command line.
And the best part of this course is that no prior knowledge of Docker or Linux is required.
10. Docker and Containers
In this course, you’ll learn how this is going to impact you as an individual as well as the teams and organizations you work for.
This course will cover Docker and containers, container registries, container orchestration, whether this stuff is for the enterprise, and how to prepare yourself for it.
These two courses from Pluralsight are not really free; you need a Pluarlsight membership to get this course, and monthly membership costs around $29 and annual membership cost around $299.
I know, we all love free stuff, but you will not only get access to this course but over 5000 courses as well, so it’s definitely the money well spent.
I have an annual membership because I have to learn a lot of new stuff all the times. Even if you are not a member, you can get this course for free by signing a free trial. Pluralsight provides 10-day free trial with no obligation.
That’s all about some of the free Docker container courses for Java developers. It’s one of the essential skill if you are developing a mobile application or web application hence, I suggest every application developer learn Docker in 2019. You will not only learn an essential skill but also take your career to the next level, given the high demand for Docker specialist and developer who knows Docker.
[Source] https://hackernoon.com/10-free-courses-to-learn-docker-for-programmers-and-devops-engineers-7ff2781fd6e0
Beginners & Advanced level Docker Training Course in Mumbai. Asterix Solution's 25 Hour Docker Training gives broad hands-on practicals
#docker swarm training#docker certification#docker training#docker training course#docker container training
0 notes
Text
Arise Server - Sql server 2012 cluster installation step by step pdf
See on Scoop.it - Arise Server
Download Sql server 2012 cluster installation step by step pdf: http://pnf.cloudz.pw/download?file=sql+server+2012+cluster+installation+step+by+step+pdf Read Online Sql server 2012 cluster installation step by step pdf: http://pnf.cloudz.pw/read?file=sql+server+2012+cluster+installation+step+by+step+pdf INTRODUCTION. 1.1 Introduction to SQL Server Failover Clustering. Organizations rely on mission-critical servers to run their businesses. As a result, server downtime can be very expensive. . For selecting a particular section in the wizard like say installation in step 2 we have to use 2 functions one is. Set-Window OS and Network Properties. This step by step is Using Windows Server 2012R2 Datacenter 64bit and SQL Server 2016 Enterprise. Edition 64bit. Network Properties. Installation of Failover Cluster Role. We need to install Failover Cluster Roles in each server of SQL. The examples in the main document are for the Microsoft Windows family, including Windows Server. 2012, Windows 7 & Windows 10. These setup instructions are for SQL Server 2016 Developer Edition, but can be used in installing other versions from 2008 and 2012 families. SQL Server Overview. You or may not have Server 2012 Failover Cluster. Introduction. This document is for StarWind and Microsoft SQL Server users who want to install and configure Failover Cluster. It provides a step-by-step procedure in configuring a 2-node. Windows Server 2012 Failover Cluster that will host a SQL Server 2012 Failover. Clustered Instance. 6 Nov 2016 This Free Ebook (pdf) provide a detailed description about setting up Failover Over Cluster for Microsoft SQL Server 2016 on Windows Server 2012 Datacenter edition. The installaiton consideration is Two Node Failover Cluster for SQL Server 2016, which can also be utilize for Shar. User Guide. Building a Microsoft. SQL Server Failover. Cluster on the Interoute. Virtual Data Centre cloudstore.interoute.com .. Clustered SQL Server Installation. . It is recommended that failover clusters are only created on the ESXi-type of VDC; however, this procedure will also work on a KVM VDC. Storage. Creating a 20 May 2014 Recently i have been preparing some articles that involve step by step guides for installing some applications that require a SQL Server for their databases, that's when i thought why not also write one about installing a highly available SQL installation which i will eventually use for my lab. So today i am 31 Dec 2012 This article is the first in a series of articles on Clustering Windows Server 2012. This first article covers the basics first steps of any cluster, regardless of whether you are clustering Hyper-V, SQL Server Failover Clusters, File Servers, iSCSI Target Server or others. Future articles will cover more detailed The goal of this documentation is to provide a step-by-step procedure in configuring a 2-node Windows Server 2012. Failover Cluster that will host a SQL Server 2012 Failover Clustered Instance. ASSUMPTIONS. When using this guide, a few assumptions have been made: • Windows Server 2012 is installed on each server 11 Mar 2018 installing sql server 2012 pdf - In this post we will be looking at the steps for Installing SQL Server. 2012 for Configuration Manager. 2012 R2. Step by step installation guide for SQL - In a previous tip on. Install SQL Server 2008 on a. Windows Server 2008 Cluster, we have seen how to install and. India Dedicated Server https://www.ariseserver.com/india-dedicated-server/
0 notes
Photo

1 Hour Hyper-V
LEARN HYPER-V IN JUST 1 HOUR
Are you looking to further your career by learning Hyper-V?
Do you want to master the fundamentals and core components of Hyper-V, but don’t want to waste 7 hours on a repetitive course, when you can learn the same in a short, to-the-point 1 hour course?
My Hyper-V for beginners course is all you need to acquire the real world job skills – that will further your career fast.
This course is a step-by-step introduction on how to enable Hyper-V on Windows 8 & 10, configure and use Hyper-V and all of it’s features, taught by an Windows Certified Professional.
Virtualization, Hyper-V console, creating virtual machines, integration services, virtual networks, hyper checkpoints & more – it’s all covered step-by-step.
This course will give you a solid theoretical understanding of Hyper-V as well as the practical skills to use it proficiently in a job.
The course is taught using Hyper-V on Windows 10, as this will teach you the core concepts of Hyper-V and is the most used version of Hyper-V in a corporate setting.
All skills taught, are directly transferable to Hyper-V on Windows 8 and Windows Server 2012 & 2016 and the few advanced differences there are, will be explained in the course.
http://texperts.it/deal/1-hour-hyper-v/
0 notes
Text
20410: Installing and Configuring Windows Server 2012 (R2 Update),thailand
20410: Installing and Configuring Windows Server 2012 (R2 Update)
20410: Installing And Configuring Windows Server 2012 (R2 Update) Course Description
Duration: 5.00 days (40 hours).
The course is part one, of a series of three courses, which provide hands-on instruction and practice on installing and configuring Windows Server 2012, including Windows Server 2012 R2. The three courses in total collectively cover implementing, managing, maintaining, and provisioning services and infrastructure in a Windows Server 2012 environment. While there is some cross-over in skillset and tasks across the courses, this course primarily covers the initial implementation and configuration of those core services, such as Networking, Storage, Active Directory Domain Services (AD DS), Group Policy, File and Print Services, and Hyper-V.
This course maps directly to and is the preferred choice for hands-on preparation for Microsoft Certified Solutions Associate (MCSA) Exam 70410:Installing and Configuring Windows Server 2012, which is the first of three exams required for MCSA: Windows Server 2012 credential.
Note: Labs in this course are based on the General Availability release of Windows Server 2012 R2 and Windows 8.1.
Intended Audience For This 20410: Installing And Configuring Windows Server 2012 (R2 Update) Course
» This course is intended for information technology (IT) Professionals who have some knowledge and experience working with Windows operating systems and who want to acquire the skills and knowledge necessary to install and perform the initial configuration of a Windows Server 2012 or Windows Server 2012 R2 server in an existing Windows server environment.
20410: Installing And Configuring Windows Server 2012 (R2 Update) Course Objectives
» Deploy and Manage Windows Server 2012.
» Describe Active Directory Domain Services (AD DS).
» Manage AD DS objects.
» Automate AD DS Administration.
» Implement IPv4.
» Implement Dynamic Host Configuration Protocol (DHCP).
» Implement Domain Name System (DNS).
» Implement IPv6.
» Implement local storage.
» Implement File and Print services.
» Implement Group Policy.
» Secure Windows servers by using Group Policy Objects (GPOs).
» Implementing Server Virtualization with Hyper-V.
20410: Installing And Configuring Windows Server 2012 (R2 Update) Course Outline
Module 1: Deploying and Managing Windows Server 2012
Windows Server 2012 R2 Overview
Installing Windows Server 2012 R2
Post-Installation Configuration of Windows Server 2012 R2
Overview of Windows Server 2012 R2 Management
Introduction to Windows PowerShell
Lab : Deploying and Managing Windows Server 2012 R2
Module 2: Introduction to Active Directory Domain Services
Overview of AD DS
Overview of Domain Controllers
Installing a Domain Controller
Lab : Installing Domain Controllers
Module 3: Managing Active Directory Domain Services Objects
Managing User Accounts
Managing Groups
Managing Computer Accounts
Delegating Administration
Lab : Managing Active Directory Domain Services Objects
Module 4: Automating Active Directory Domain Services Administration
Using Command-line Tools for AD DS Administration
Using Windows PowerShell for AD DS Administration
Performing Bulk Operations with Windows PowerShell
Lab : Automating AD DS Administration by Using Windows PowerShell
Module 5: Implementing IPv4
Overview of TCP/IP
Understanding IPv4 Addressing
Subnetting and Supernetting
Configuring and Troubleshooting IPv4
Lab : Implementing IPv4
Module 6: Implementing Dynamic Host Configuration Protocol
Installing a DHCP Server Role
Configuring DHCP Scopes
Managing a DHCP Database
Securing and Monitoring DHCP
Lab : Implementing DHCP
Module 7: Implementing DNS
Name Resolution for Windows Clients and Servers
Installing a DNS Server
Managing DNS Zones
Lab : Implementing DNS
Module 8: Implementing IPv6
Overview of IPv6
IPv6 Addressing
Coexistence with IPv4
IPv6 Transition Technologies
Lab : Implementing IPv6
Module 9: Implementing Local Storage
Overview of Storage
Managing Disks and Volumes
Implementing Storage Spaces
Lab : Implementing Local Storage
Module 10: Implementing File and Print Services
Securing Files and Folders
Protecting Shared Files and Folders by Using Shadow Copies
Configuring Work Folders
Configuring Network Printing
Lab : Implementing File and Print Services
Module 11: Implementing Group Policy
Overview of Group Policy
Group Policy Processing
Implementing a Central Store for Administrative Templates
Lab : Implementing Group Policy
Module 12: Securing Windows Servers Using Group Policy Objects
Windows Operating Systems Security Overview
Configuring Security Settings
Restricting Software
Configuring Windows Firewall with Advanced Security
Lab : Increasing Security for Server Resources
Lab : Configuring AppLocker and Windows Firewall
Module 13: Implementing Server Virtualization with Hyper-V
Overview of Virtualization Technologies
Implementing Hyper-V
Managing Virtual Machine Storage
Managing Virtual Networks
Lab : Implementing Server Virtualization with Hyper-V
a
0 notes
Text
67% off #Learn to Build Apps for Facebook and Chrome Store – $10
The complete guide to create and publish your apps on Facebook and Chrome store
Intermediate Level, – 6 hours, 32 lectures
Average rating 4.5/5 (4.5 (12 ratings) Instead of using a simple lifetime average, Udemy calculates a course’s star rating by considering a number of different factors such as the number of ratings, the age of ratings, and the likelihood of fraudulent ratings.)
Course requirements:
Internet connection and a zeal to learn.
Course description:
Web Apps are the future. They present a great new opportunity for developers worldwide to reach millions of app hungry consumers. Facebook being the big daddy of social networks present a great opportunity to monetize your idea by building apps for this amazing platform. Chrome is the popular kid with lot of fan following and with a thriving marketplace it too provides an opportunity which should not be missed. We at Eduonix Technologies are always working on creating content which help our students not only enhance their skill but monetize their ideas. This course of ours is aimed towards professionals and hobbyists alike. It will teach you to take your web programming knowledge to next logical step – web app development and monetization.
You start with basic introduction to web technologies and then work towards creating apps which you can put on the market place by the end of the course. So go ahead and take the leap. Be the great app developer you always wanted to be!
Full details To create apps for Facebook and Chrome Understand use of the web technologies like Javascript, HTML5, CSS, JSON and PHP Understand the app development cycle for Facebook Understand the app development cycle for Chrome store Basic knowledge of web programming
Reviews:
“I struggled to follow along with some of the Facebook sections as the course material wasn’t up to date with how Facebook works now. I wanted an intro though, and this was good enough for that. One star removed for time wasting having to find work-arounds.” (Adam Archer)
“I think that this course is for guys who wants a basic intro to the FB & Chrome app development. The course covers much of the basic aspects of the subject. I actually wanted to give 4,5 (four and a half star) to the course, because I really would like to see how to publish to user wall without dialog boxes, but as you know there is no type of rating here I gave it 5.” (İnan Madak)
“Great course to get started with Web App Development. I was looking for a similar course for quite some time. It has all the ingredients to get me started with FB app development.” (Adam)
About Instructor:
Eduonix Learning Soultions Eduonix-Tech .
Eduonix creates and distributes high quality technology training content. Our team of industry professionals have been training manpower for more than a decade. We aim to teach technology the way it is used in industry and professional world. We have professional team of trainers for technologies ranging from Mobility, Web to Enterprise and Database and Server Administration.
Instructor Other Courses:
Projects In ReactJS – The Complete React Learning Course Eduonix Learning Soultions, 1+ Million Students Worldwide | 200+ Courses (17) $10 $40 Implementing and Managing Hyper-V in Windows Server 2016 Eduonix Learning Soultions, 1+ Million Students Worldwide | 200+ Courses (1) $10 $20 Learn to build an Auth0 App using Angular 2 Youtube: Beginners Guide To A Successful Channel Learn To Build A Google Map App Using Angular 2 Learn Web Development Using VueJS …………………………………………………………… Eduonix Learning Soultions Eduonix-Tech . coupons Development course coupon Udemy Development course coupon Mobile Apps course coupon Udemy Mobile Apps course coupon Learn to Build Apps for Facebook and Chrome Store Learn to Build Apps for Facebook and Chrome Store course coupon Learn to Build Apps for Facebook and Chrome Store coupon coupons
The post 67% off #Learn to Build Apps for Facebook and Chrome Store – $10 appeared first on Course Tag.
from Course Tag http://coursetag.com/udemy/coupon/67-off-learn-to-build-apps-for-facebook-and-chrome-store-10/ from Course Tag https://coursetagcom.tumblr.com/post/158221999998
0 notes